
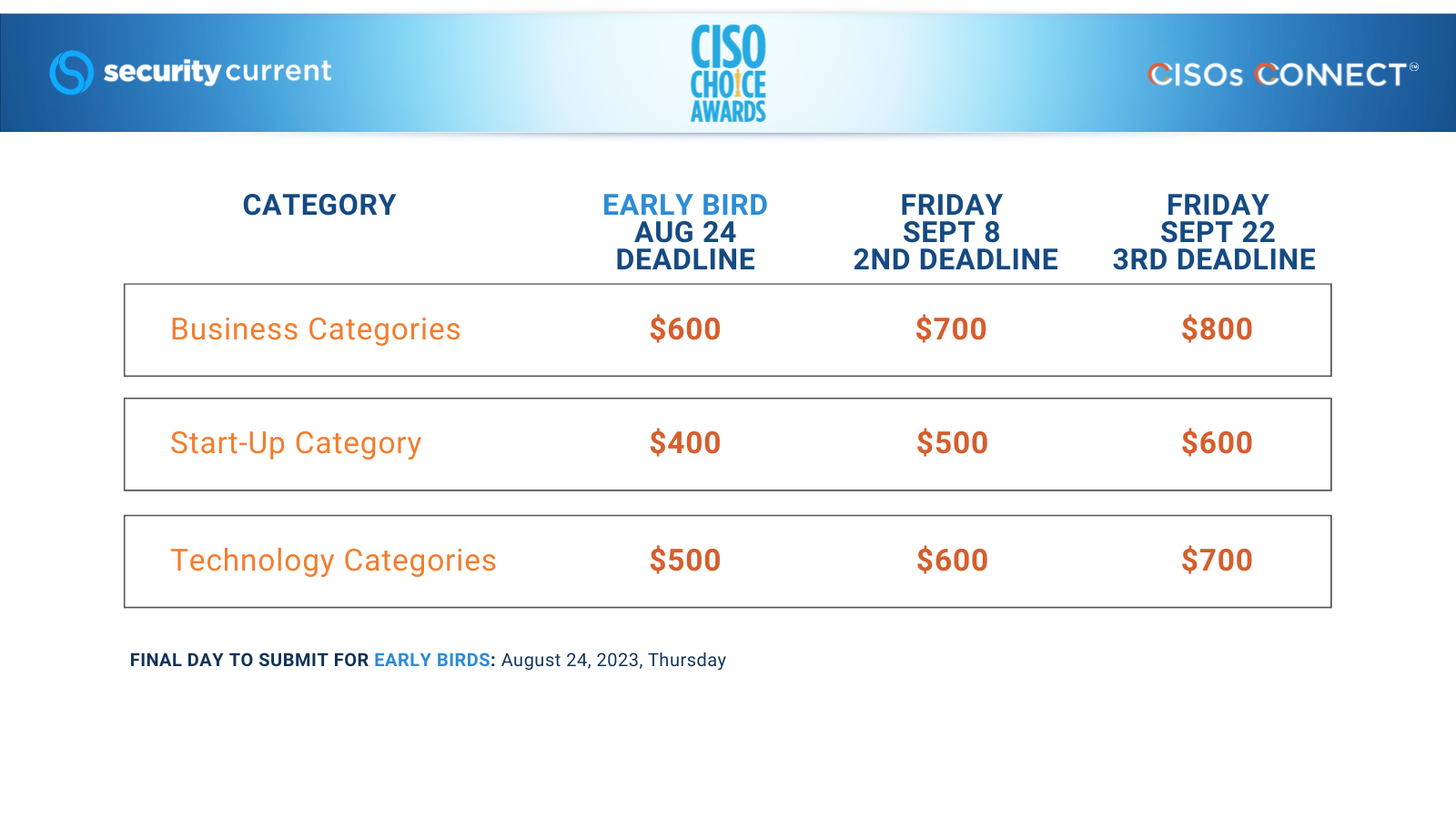
Following are the categories and information on the submission fee.
You may submit to multiple categories, each with their own fee:
CISO CHOICE AWARDS FEES
BUSINESS CATEGORIES
Best Use of AI - NEW
Generative AI is having a dramatic impact on security products as they take the first steps to use large language models to improve the understanding of raw data from logs and telemetry. This category is for the vendors that have made the best use of generative AI in their products to reduce hunt time, find problems quicker, and create playbooks on the fly.
Visionary Vendor
Established vendor or start-up whose solutions are built on technologies that can evolve with the CISOs’ needs or solutions that are forward-looking, to address potential new threats.
Premier Security Company
Established vendor that is providing either overarching security solutions or solutions that help safeguard key security components in a CISO’s infrastructure.
Start-up Security Company
A company whose solution has been in beta or generally available for under 2 years.
Partner in Success
Providers who have working relationships with CISOs or their employees to meet their needs of today while being responsive to the CISOs’ enterprises’ changing needs.
TECHNOLOGY CATEGORIES
