
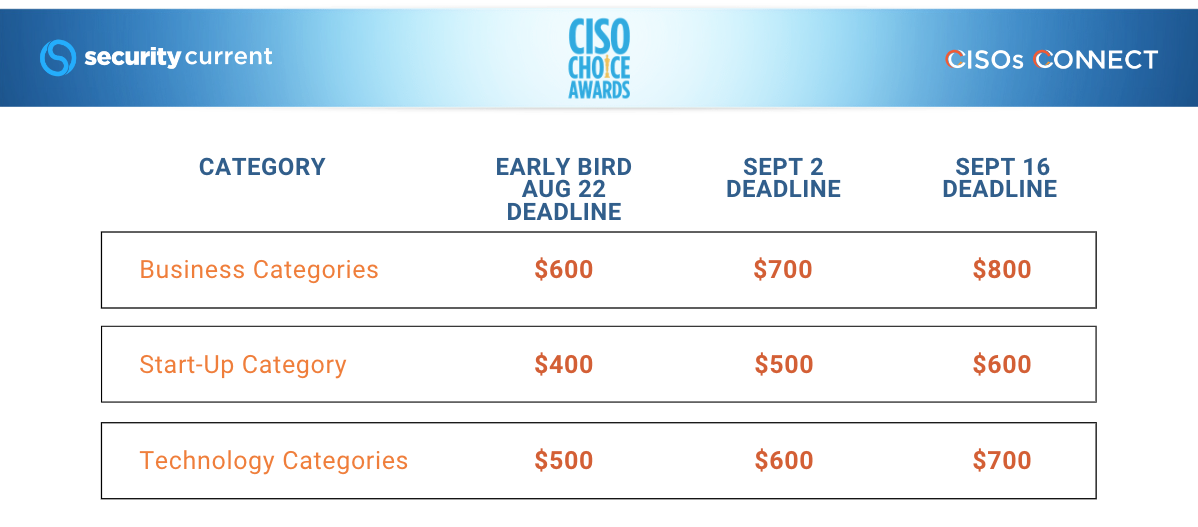
Following are the categories and information on the submission fee.
You may submit to multiple categories, each with their own fee:
CISO CHOICE AWARDS FEES
BUSINESS CATEGORIES
Visionary Vendor
Established vendor or start-up whose solutions are built on technologies that can evolve with the CISOs needs or solutions that are forward-looking, to address potential new threats.
Premier Security Company
Established vendor that is providing either overarching security solutions or solutions that help safe-guard key security components in a CISOs’ infrastructure.
Start-up Security Company
A company whose solution has been in beta or generally available for under 2 years.
Partner in Success
Providers who have working relationships with CISOs or their employees to meet their needs of today while being responsive to the CISOs’ enterprises’ changing needs.
TECHNOLOGY CATEGORIES
API Security - NEW
These solutions offer standalone capabilities and are separate from application security. They touch on code but are not only about the code.
Application Security (included DevSecOps)
This includes DevSecOps as well as the tools for code analysis, putting apps in containers, and hardening apps, etc.
Breach and Attack Simulation - NEW
These solutions are part of a CISOs’ fast-growing operations security program.
Cloud Security Posture Management - NEW
This is the fastest growing, most highly invested segment in security that includes solutions from CSPM in AWS, Azure, GCP, Google Cloud Platform, and OpenStack.
Cloud Security Solution
There are primarily two types of vendors in cloud security. Those that serve their solution from the cloud, or SaaS, instead of an on-premises license and those that offer protections for cloud workloads including firewalls, WAFs, and encryption.
Cloud Workload Protection Platform - NEW
These solutions are the modern endpoint security for the cloud and can be agent or agentless.
Data Security
Data security includes vendors from database protection to encryption as well as Digital Rights Management (DRM), Information Rights Management (IRM), Data Loss Protection (DLP) and data discovery and classification.
Email Security (Phishing)
Email is a separate category because it crosses the bounds of endpoint, network and data security. It includes email encryption as well as anti-phishing, anti-spam, blocking business email compromise, and outbound email security.
Endpoint Security
Endpoint security includes the vendors that provide anti-malware solutions, endpoint monitoring or Endpoint Detection and Response (EDR), configuration management, server monitoring and protection, and even vulnerability management and container security. This category includes mobile device security vendors.
Fraud Prevention
Fraud prevention is of particular interest to financial services and ecommerce buyers. Customer behavior, reputation, authentication, and CAPTCHAs are included in this category.
Governance Risk and Compliance (GRC)
GRC is a broad category that includes measuring and reporting risk in ways that are compatible with various compliance regimes.
Identity and Access Management (IAM)
IAM includes all of the authenticators, from 2FA to typing patterns and biometrics. It also includes the identity stores, and directory services.
IoT Security
Solutions that secure a myriad of verticals from medical to industrial to automotive to critical infrastructure to business systems and more. They can be solutions that are securing new IoT or solutions CISOs can use to secure existing infrastructure.
MSSP
Network Security
From next-generation firewall hardware appliances to cloud-traffic analysis, network security is the biggest security vendor space and the first line of defense against attacks.
Passwordless - NEW
These solutions provide rapidly evolving ways to accomplish strong authentication.
Risk Management
SASE - NEW
These solutions are a complete replacement of the data center security stack.
Security Analytics
Threat hunting, correlation, visualization, graph analysis are all included in this category. All are used to help the SOC engineer do their job.
Security Awareness Training (for the Everyday Employee) - NEW
These solutions provide training exercises (i.e. anti-phishing simulations), educational videos, and information security awareness training.
Security Education/Training (Security Certifications)
Solutions in this category teach security skills for CISOs and their teams and provide certifications.
Security Operations
Security Operations includes SOAR, Orchestration, and tools to enable the SOC.
Third Party Risk Management (TPRM) - NEW
These solutions help CISOs extend their policies to their supply chain.
Threat Intelligence
Solutions include those that gather activity on threat actors. It includes platforms that combine and rationalize feeds as well as those vendors that use open source intelligence, Dark Web monitoring and Domain Name System (DNS) to create those feeds.
Vulnerability Management
The plethora of scanning tools that identify when a vulnerable application or Operating System (OS) is deployed.
