Application security is in crisis. Some shocking statistics to help set the stage… The average organization has hundreds or thousands of applications spanning many millions or even billions of lines of code, the average application has 26.7 serious vulnerabilities, 82% of breaches in financial organizations are due to applications, and the average breach costs $4m.[1] With roughly 20 million developers worldwide, we’re producing vulnerable code faster than ever before.
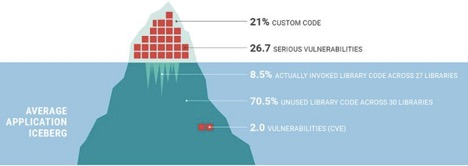 Source: State of Application Security: Libraries & Software Composition Analysis
Source: State of Application Security: Libraries & Software Composition Analysis
DevOps is a “systems thinking” approach to unifying tasks traditionally owned by application development, operations teams, and other traditional “silos.” DevOps has shown dramatic benefits for software development: 200x more frequent deployments, 24x faster recovery from failures, 3x lower change failure rate, and 22% less unplanned work and rework.[2] Perhaps the secret to effective security can be found in DevOps too.
DevOps alone doesn’t really have anything to do with security. But maybe we can translate our security challenges into problems that DevOps can help with. To do this, we’ll translate the “Three Ways” of DevOps for security. We need a revolution in application security, or we will continue to fail.
“The First Way of Security” – Establish security work flow
First, we’re going to think of application security as a concrete thing that needs to be delivered to customers. The final form might look like a report or dashboard, but it’s all the work to get to that result that matters.
One simple goal might be that every application will be continuously monitored to ensure that:
- All the right defenses are in place and working
- No vulnerabilities have been introduced
- Attacks are being detected and triaged
- Defenses for new vulnerabilities and attacks can be deployed in a few hours
Currently organizations rely on giant scans at the end of the application development process. However, by doing periodic scans during the lifecycle, we can break it down into smaller pieces and deliver incremental results.
Consider reorganizing security work to focus on a single risk at a time. Pick your most significant risk and establish continuous threat modeling, implementing defenses, security testing, monitoring, and response. With this workflow, organizations can quickly receive a working defense needed for a single risk, as well as the infrastructure required for continuous assurance that it is effective.
“The Second Way of Security” – Ensure instant security feedback
Next, let’s establish tight feedback loops that prevent risks from getting out of control (and expensive). The typical organization has very long application security feedback loops, sometimes annual, sometimes triannual, before problems get identified and fixed.
With newer continuous application security technologies like Interactive Application Security Testing (IAST) and Runtime Application Self-Protection (RASP), organizations can assess and monitor all their applications in parallel. We can establish a security notification “bus” that connects security checks across the software development lifecycle (SDLC) to all the people who need that information, through the tools they are already using, like JIRA, Slack, Eclipse, Jenkins, Splunk, and more.
“The Third Way of Security” – Encourage a security culture
Finally, imagine a culture of “security in sunshine” by celebrating both vulnerabilities and attacks as opportunities to learn, without fear of retribution. Resist the temptation to hide details of both vulnerabilities and attacks.
Instead, double-down on making your entire business aware of exactly who is attacking you, what attack vectors they are using, and what applications and APIs they are targeting. Encourage all your teams to learn about vulnerabilities and attacks and ensure that the right defenses are in place. A culture of security experimentation and continuous learning can ensure quick response to new and emerging threats.
Whenever possible, stamp out security exceptionalism and empower development teams to build security (and assurance) the way they build everything else.
Reimagine security today
DevOps has had a remarkable effect on software development. But application security is still lagging behind with monolithic, waterfall-style security processes. By ensuring that security work has a direct line of sight to real business concerns, repeated and wasted work can be eliminated.
The DevOps revolution has paved the way for application security to reinvent itself. Can we rally around this cause and ensure that the software we leave behind for our children is more secure than what we have today?
A pioneer in application security, Jeff Williams has more than 20 years of experience in software development and security. He is the co-founder and Chief Technology Officer of Contrast Security, developer of a revolutionary application security product that enhances software with the power to defend itself, check itself for vulnerabilities, and join a security command and control infrastructure. Williams is also a founder and major contributor to OWASP, where he served as the Chair of the OWASP Board for 8 years and created the OWASP Top 10, OWASP Enterprise Security API, OWASP Application Security Verification Standard, XSS Prevention Cheat Sheet, and many other widely adopted free and open projects.

