As cybersecurity matures as an industry, network defenders understand that preventing attack, while best case, is not foolproof. However, just because an adversary compromises a machine does not mean the battle is lost. In fact, it has just begun. In this article, I’ll describe how evolving your cybersecurity strategy from singleton instance detection to detecting attack patterns in your network can turn the tables on your adversary and thwart their game plan.
Evolving Your Cybersecurity Strategy
Just as cyber adversaries are evolving their strategy and tactics, as a defender you must develop a strategy to evolve your security defenses. We know that any attacks you can prevent, you should. However, we also know it is not feasible to prevent all attacks.
In fact, the odds favor the adversary when it comes to initial compromise. The adversary must find only one weakness – typically an employee on the network – while the defender must close all potential avenues to compromise. This asymmetry in level of effort pretty much guarantees a motivated adversary can always gain an initial beach head on a network. On the other hand, once the adversary gets on your network, the game has only just begun and, counter-intuitively, the odds now favor the defender.
When it comes to evolving your strategy, Figure 1 shows where the security industry has come from and where it is likely going. The staples of enterprise security prevention technology are endpoint anti-virus and network firewalls. The good news about these devices is they have become smarter.
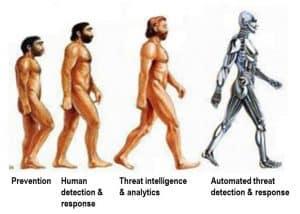
Figure 1: Evolving Cyber Strategy
Now, anti-virus and firewalls continually are fed cloud-based threat intelligence to stay on top of the latest threats. And many are powered with machine learning models that make it possible to detect and block previously unknown malware. The value of these devices, of course, is every compromise you stop is one less you have to respond to. So, stopping more threats before they get a foothold on the network reduces the funnel of events that need to be followed up on.
However, in the absence of perfect prevention, the need for detection and incident response drove the next evolution wave in security: human-centric detection and response. Security Operations Centers (SOCs) are the hub of enterprise security that drive detection and response efforts, typically by orchestrating the stream of machine-driven alerts and human analysis to yield actionable tasks for threat hunters and incident response specialists to follow up on.
To power these human analyst teams, a veritable market for threat intelligence feeds is driving the third wave of evolution in security: threat intelligence and security analytics derived from open source or specialized threat intelligence firms. A highly functional SOC team powered by timely and relevant threat intelligence represents state of the art in enterprise security today, and how far the security evolution has come. But even state of the art capability in threat detection and response does not put up significant barriers for motivated adversaries to achieve their goals.
To this end, the fourth wave of evolution in security will automate threat analysis and response by examining attacker patterns across network devices out of necessity to address the increasing automation and machine time scales adversaries are beginning to adopt.
Understanding Your Adversary’s Game Plan
Most adversary compromise is detected when a specific file is detected, such as a backdoor Trojan, or when an outbound request to a known malicious URL or IP is found in firewall logs. While finding malware is critical, it is in fact detecting one move in a larger game plan taking place on the network.
As illustrated in Figure 2 from MITRE’s ATT@CK framework, the adversary’s game plan starts well before the network is breached, and continues long after the initial compromise takes place.
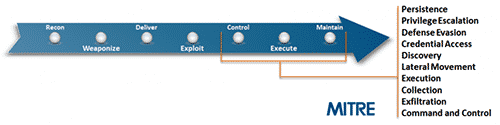
Figure 2: Adversary moves as part of overall game plan.
The highlighted section in Figure 2 shows the number of moves an adversary will often make on a victim network after initial compromise as part of the standard game plan to find and exfiltrate data. For an adversary to successfully execute his game plan, he will use some combination of techniques to gain persistence, escalate and gain network privileges, evade detection, discover the objective, and move laterally across the network to collect, archive, and ultimately exfiltrate the objective data. In the process of making all these moves, the adversary will leave digital footprints across the network.
Note that one type of attack — destructive attacks intended to destroy networks as part of cyber warfare or ransomware campaigns — will typically shorten the number of steps the adversary takes to achieve his objective, and as a result, requires far more automated prevention and response steps to deal with the short timeline.
Understanding the adversary’s game plan will empower network defenders to develop their own game plan to counter the adversary. In fact, once the adversary is on your network, the playing field advantage reverses to favor the defender. When the adversary is on your turf, you have the opportunity to detect and stop the adversary because of the number of moves the adversary needs to make to achieve his objective in unfamiliar terrain. This window of opportunity provides the ability to collect these digital footprints, to analyze them, and then take action to stop the adversary from successfully completing his mission; for example, by implementing quarantine or containment strategies.
By having home field advantage, you own the “high ground” on your network from which to observe and prosecute the adversary. This requires you to understand where your company assets are — ones that are likely being targeted — and the ability to instrument the network with sensors and tripwires to detect when an adversary is executing his game plan. The strategy also allows you to set traps to lure an adversary into revealing himself by taking advantage of the fact you understand your network and company assets while your adversary must discover them.
Inflicting Pain on the Adversary
With the insight that you gain advantage once the adversary is on your network, coupled with understanding your adversary’s game plan, you can develop a strategy for countering the adversary. The current state of play here is in the third wave of security — threat intelligence & security analytics — but it should become clear that this will drive the fourth wave, automated threat detection and response, as technology matures and out of sheer necessity.
Remembering that the adversary is human, and humans are fundamentally lazy, you can develop strategies that counter the adversary by inflicting pain (time, labor, cost) on his efforts. David Bianco’s Pyramid of Pain chart is useful for understanding the factors that impact the adversary’s work.
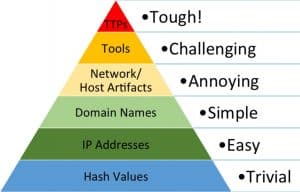
Figure 3: An Attacker’s Pyramid of Pain
The pyramid in Figure 3 represents a view of adversary observables from a defender’s point of view in order of difficulty for the adversary to change. The area in each segment of the pyramid is also roughly proportionate to how much information is available about threats. At the bottom of the pyramid are the three types of information widely shared among threat intelligence organizations today: file hashes, IP addresses, and domain URLs. Not coincidentally, this data, also called Indicators of Compromise or IOCs, is easily and automatically changed by the adversary via toolkits. While detecting an adversary via these indicators can be accomplished with today’s products, detection is also relatively simple to evade for adversaries.
As you go up the pyramid, host and network artifacts left by the adversary – for example, registry keys, directory structures, distinctive user agents, and SMTP headers, among other artifacts – together become signatures of an attack that can be used to detect adversarial presence. Adversaries invest in tools, and detecting their tooling is one sure fire way to detect their presence. For example, categorically detecting exploits generated from Metasploit or Cobalt Strike toolkits is one way to force the adversary to move to more custom tooling, which is very costly.
At the top of the pyramid is adversary tactics, techniques, and protocols (TTPs). This is essentially the modus operandi of the adversary which is the way the adversary behaves on the network, beyond individual artifacts. Characterizing and cataloging adversary behavior patterns is the first step to detecting them on your network. The good news is it is very difficult and costly for the adversary to change his TTPs.
To provide a physical world analogy, if you try to detect a bank robber based on the clothes he wore in his last heist, you run the likely risk he will change his clothes on his next heist. On the other hand, if you were able to fully characterize his modus operandi, and physical characteristics such as his gait, and then used analytics on video streams to analyze gait with high precision, it would be very difficult for him to change his gait over a sufficient sampling.
Fortunately, work in characterizing adversary patterns has already begun and is captured in MITRE’s cyber analytics repository. The site is a curated set of adversary analytics that can be described as adversary behavior patterns mapped to host and network observables. The analytics are also mapped to the ATT@CK framework, the adversary’s game plan.
Admittedly, as an industry we are still in the early stages of characterizing adversary attack patterns. But with community curated efforts like the cyber analytics repository, we can begin to characterize the adversary TTPs, which is a necessary first step to detecting adversarial attack patterns on your network.
Charting the Course to the Next Evolution in Security
The state of the art in cybersecurity operations is highly functional teams applying timely and relevant IOCs to logs in order to find adversaries on networks. This works to some extent because much of hacking is still human driven. However, as adversaries adopt artificial intelligence and begin automating their exploits, the time line from exploit to exfiltration will shrink, potentially dramatically. What may take weeks today to find and capture the flag (so to speak) for an adversary, will take mere hours or less in the future.
The next evolution in cyber security will leverage the work that has begun in characterizing adversary behavior patterns and build models from this intelligence into products that work together to detect and contain threats. The work of analysts today will be performed by AI algorithms out of necessity against vast data sets in the cloud captured from endpoints and firewalls to find adversary attack patterns.
Product sets will work together to capture digital footprints of adversaries across the network and share these insights in the cloud, where big data algorithms will mine them for attack patterns. In turn, these insights will be consumed by products, such as endpoints and network firewalls, to stop attackers from achieving their ultimate objective.
The evolution will change the point of view security products take from detecting single artifacts of attacks such as malware, to collecting and analyzing digital footprints to find attack patterns, and then synchronizing actions among products to contain adversaries before they can cause material harm to enterprises.

